Today, I spent half my day debugging an email error. I got a lot of bounces saying:
552 5.2.0 Message contains bare CR and is violating 822.bis section 2.3 (in reply to end of DATA command))In the 20+ years I'm running mailservers, I had never heard of this error before. And Google couldn't make me much wiser either.
The mailserver generating the message was mxin5.ziggo.nl - the primary server for Dutch provider Ziggo. I could not figure out which MTA they are using, although the banner right after an EHLO looks like Sendmail. I downloaded the latest Sendmail sources, but this error message does not come from a vanilla Sendmail installation. Other software like FortiMail may be a Sendmail fork or mimic the Sendmail signatures. But of course we cannot examine their source code.
I did find some references that qmail may have problems with bare LFs. But those were with regards to LF (line feed), not CR (carriage return). Downloaded the source of qmail and netqmail to find that qmail was probably not the MTA used either.
Then I tried to trace my own postfix server. Let's see that the mail does indeed contain a bare CR. I did not believe there was a bare CR as I examined the sourcecode of the generating software. Tracing is a lot harder nowadays since starttls will prevent a simple tcpdump. As an alternative, I used postfix' header_checks to HOLD a suspected mail and sure enough, the software generating the message included a stray CR = hex char %0D = \r in a small percentage of outgoing mails. The generating software used an external data source which inserted the CR.
The bug generating the CR in the emails is years old, the mails were always accepted by Ziggo without any problem. My best guess is that Ziggo recently upgraded their mailserver and the new version now forbids the CR.
© GeekLabInfo 552 5.2.0 Message contains bare CR and is violating 822.bis section 2.3 (in reply to end of DATA command)) is a post from GeekLab.info. You are free to copy materials from GeekLab.info, but you are required to link back to http://www.geeklab.info

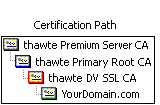 Normal "single root" certs are only certified by one single parent which is recognised by clients immediately. Chained certs on the other side are signed by a parent which itself is signed by another parent. This effectively makes your cert a "grandchild" of the CA root. In the image attached you'll see a cert that is chained by two intermediate certs.
Normal "single root" certs are only certified by one single parent which is recognised by clients immediately. Chained certs on the other side are signed by a parent which itself is signed by another parent. This effectively makes your cert a "grandchild" of the CA root. In the image attached you'll see a cert that is chained by two intermediate certs.