When experimenting with IPv6 this weekend, I thought it would be cool to give my IPv4-only devices such as my webcam an IPv6 address.
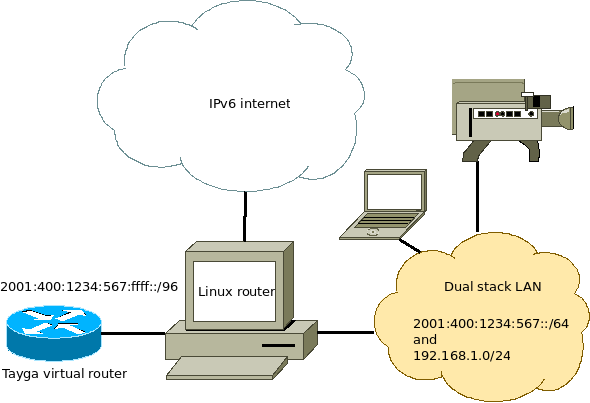
Using Tayga to do NAT64, I could route an IPv6 range to a virtual network interface where Tayga translates incoming packets to IPv4. As Tayga's documentation states: "You will need to select an unused /96 from your site's IPv6 address range which will be used as the NAT64 prefix." Unfortunately, I only have one single /64 available, a range that should not be split.
What I did, was the following:
This is not really best practice, as hosts in the range 2001:400:1234:567:ffff:0:0:0 - 2001:400:1234:567:ffff:ffff:ffff:ffff could be located on both the LAN and the Tayga virtual router, it's the only working method for the time being.
The Linux router sends packets for 2001:400:1234:567:ffff::/96 to Tayga instead of direcly to the lan. This works for outside hosts, but hosts on the LAN don't know that packets for this range should be sent to the Linux router. They try to find my webcam on the LAN, but obviously can't find it.
Neighbour discovery
This looking for the webcam on the LAN is called neighbour discovery. The Neighbour Discovery Protocol performs functions similar to IPv4 ARP for finding other nodes on the same LAN. With above setup, the host at 2001:400:1234:567:ffff::1 is actually off the LAN. The Linux router must tell my laptop to send packets for this IP to the router.
proxy_ndp
You can do this using proxy_ndp, the IPv6 variant of proxy_arp. First enable proxy_ndp by running:
sysctl -w net.ipv6.conf.all.proxy_ndp=1 |
You can enable this permanently by adding the following line to /etc/sysctl.conf:
net.ipv6.conf.all.proxy_ndp = 1 |
Then run:
ip -6 neigh add proxy 2001:400:1234:567:ffff::1 dev eth0 |
This means for the Linux router to generate Neighbour Advertisement messages in response to Neighbour Sollicitation messages for 2001:400:1234:567:ffff::1 that enter through eth0. Note that 2001:400:1234:567:ffff::1 itself is not found on eth0, but on another virtual interface.
ndppd - NDP Proxy Daemon
While proxy_arp could be used to proxy a whole subnet, this appears not to be the case with proxy_ndp. To protect the memory of upstream routers, you can only proxy defined addresses. There is a daemon that can proxy a whole subnet, ndppd. It's available at
http://priv.nu/projects/ndppd/.
Links
Another interesting page on this subject is found at:
http://linux-attitude.fr/post/proxy-ndp-ipv6
(French, use google translate) - multiple /64's in a /56
http://wiki.stocksy.co.uk/wiki/IPv6%2BXen_on_a_Hetzner_server_with_routing_to_dummy0_and_proxy_ndp - exactly what I'm doing, but for other purposes. Just found this page after typing my own.
© GeekLabInfo IPv6 neighbour proxy is a post from GeekLab.info. You are free to copy materials from GeekLab.info, but you are required to link back to http://www.geeklab.info